Credit to MK/MG
Nintendo DS Reversing 500
There is a simple space shooter and a boss with a lot of health represented with the red bar at the top. Each time you shoot you do 2 damage (1 for each bullet) and he has a lot of health.
Using ArtMoney and NoCashGBA you can find the value of the bosses health to be 1000000. Search for an unknown value, shoot the boss, say the value decreased, reload the rom, say the value increased and repeat until you only have a few values.
Discover 2032178 = boss health
Start the rom, modify the value, Kill the boss, and get a screen that says KEY IS DUGZFG. The hint says are you sure you have the full key?
Keep modifying the bosses health after the screen loads and eventually you will get it to say KEY IS DUGZFGJCRC. This is a trap.
The key is really printed with text in memory and not to the screen.
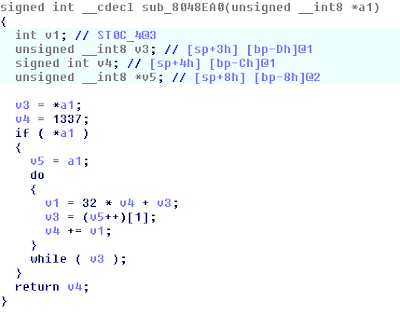
Using IDA PRO with a NDS Loader
Load Strings and find where GameInit is loaded in sub_20019B8.
Notice WinState is loaded by sub_2001c40.
Right click the gameinit sub and find references to sub 2001dcc
Press space on the call to BL #0x20019B8 and get the memory address 0x2001DE8
So if you modify BL sub_2001920 to BL sub_2001c40 it will load the win state instead of the game. Cool let's make that change.
View the opcodes under options general and set the number of opcode bytes to 8.
Open HXD and search for that place in the program. 04 1c 20 1c ff f7 E6 FD 20 1C.
Open sub_2001c40 in ida and find references to it in sub_200220c
Press space BL sub_2001c40 and notice its opcodes are FF F7 9F Fb
Change "FF F7 E6 FD" to "FF F7 9F FB"
Save the file and run this in Desmume.
Click on the black screen to start the Win State. You won't see anything because of how kiwi made the rom using devkitpro.
Dump the memory for the ds in desmume using the memory utility
Strings the memory dump and search for key
You will find "key is ou6UbzM8fgEjZQcRrcXKVN"